A massive cache of leaked data exposes the inner workings a stalkerware operation spying on thousands of people all over the globe, including Americans.
The leaked data includes call logs and text messages of unsuspecting victims. Their Android phones and tablets were compromised with a number of similar stalkerware apps including Copy9, MxSpy, TheTruthSpy and many others.
These Android apps can be planted by someone who has physical access to a device. They are intended to remain hidden on the home screen of the user but silently and continuously upload their contents to the phone.
SPYWARE LOOKUP TOOL
Here you can find out if your Android tablet or phone has been compromised.
Months After we published our investigation into the stalkerware operation’s activities, a source gave TechCrunch tens to gigabytes data from stakerware’s servers. The cache includes the stalkerware operation’s core database. This contains detailed records of every Android device that was compromised since early 2019 (though some data dates back earlier), and which device data was stolen.
Given that the victims didn’t know that their device data had been stolen, TechCrunch retrieved every device identifier from the database and created a lookup tool that allows anyone to see if their device has been compromised by any stalkerware apps. This tool was available up to April 2022, when the data was dumped.
TechCrunch analyzed the remainder of the database. We used mapping software to analyze the geospatial data and plotted thousands of locations from the database. TheTruthSpy has a vast network of victims, on almost every continent. TheTruthSpy stalkerware is a grey area, which makes it difficult for authorities to fight it, despite the increasing threat it poses to victims.
First, some information about the data. The database is about 34 gigabytes in size and consists of metadata, such as times and dates, as well as text-based content, like call logs, text messages and location data — even names of Wi-Fi networks that a device connected to and what was copied and pasted from the phone’s clipboard, including passwords and two-factor authentication codes. The database didn’t contain media, images or videos taken from victims’ devices. Instead, it logged information about each file such as the date and time of its creation, call durations, and even phone numbers. This allowed us to track how much content was stolen from victims’ phones and how long. Each device compromised uploaded different amounts of data depending upon how long they were compromised and the available network coverage.
TechCrunch examined the data spanning March 4 to April 14, 2022, or six weeks of the most recent data stored in the database at the time it was leaked. It is possible that TheTruthSpy’s servers retain only certain data such as location and call logs for a few weeks but not other content like photos or text messages for longer.
This is what we found.
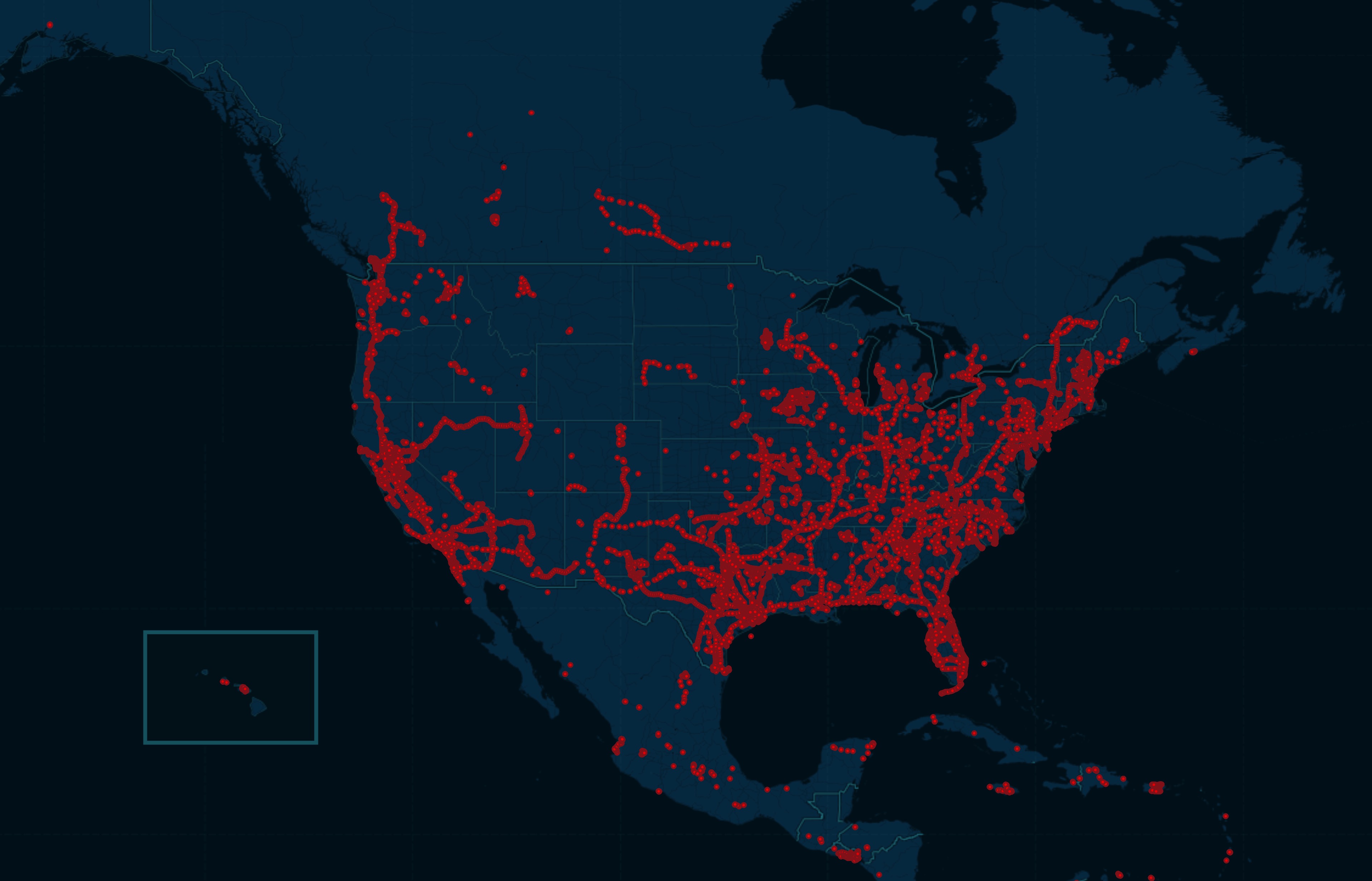
This map shows six weeks of cumulative location data plotted on a map of North America. This map shows six weeks of cumulative location data plotted on a map of North America. It includes victims who live in major cities and urban centers, as well as those who travel on major transport lines. Image Credits: TechCrunch
The database has about 360,000 unique device identifiers, including IMEI numbers for phones and advertising IDs for tablets. This number indicates how many devices have been compromised and how many people were affected by the operation. The database also contains the email addresses of every person who signed up to use one of the many TheTruthSpy and clone stalkerware apps with the intention of planting them on a victim’s device, or about 337,000 users. This is because certain devices could have been compromised multiple times (or by another stalkerware app), and some users may have more than one compromised device.
About 9,400 new devices were compromised during the six-week span, our analysis shows, amounting to hundreds of new devices each day.
The database stored 608,966 location data points during that same six-week period. To show the global spread of compromised devices, we plotted the data and created an animation. This was done to show how large-scale TheTruthSpy is. To protect individual privacy, the animation zooms out to the global level. However, the data is very granular and shows victims at transport hubs, places to worship, and other sensitive locations.
By breakdown, the United States ranked first with the most location data points (278,861) of any other country during the six-week span. India had the second most location data points (77,425), Indonesia third (42,701), Argentina fourth (19,015) and the United Kingdom (12,801) fifth.
Canada, Nepal, Israel, Ghana and Tanzania were also included in the top 10 countries by volume of location data.
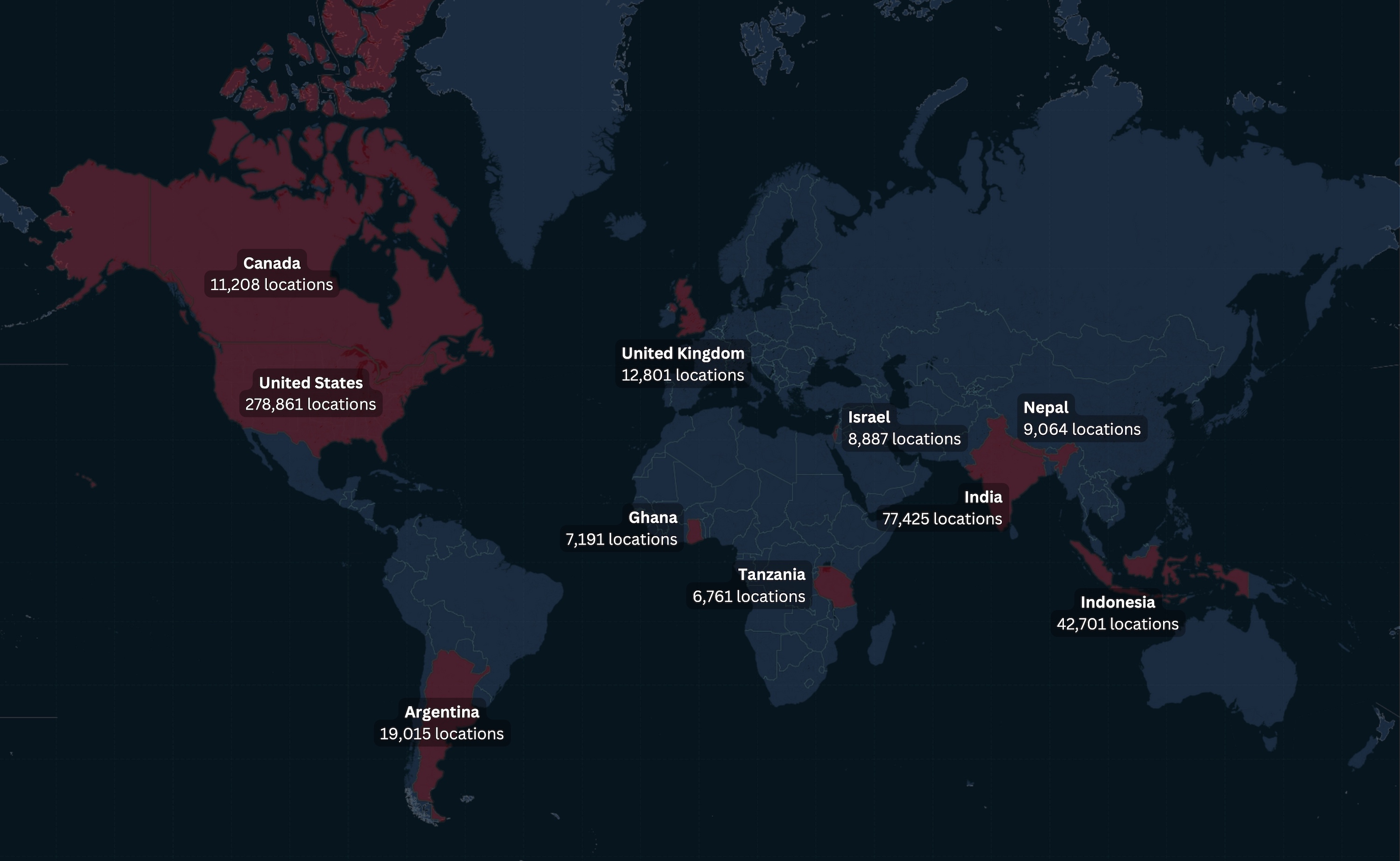
This map shows the total number of locations ranked by country. The U.S. had the most location data points at 278,861 over the six-week span, followed by India, Indonesia, and Argentina, which makes sense given their huge geographic areas and populations. Image Credits: TechCrunch
The database contained 1.2 million text messages. This includes the contact name and 4. 42 million call logs during the six-week span, including detailed records of who called whom, for how long, and their contact’s name and phone number.
TechCrunch found evidence that data was likely to have been collected from children’s phones.
These stalkerware apps also recorded thousands of calls over the six-week period, according to the data. The database contains 179,055 entries of call recording files that are stored on another TheTruthSpy server. To determine the location of calls recorded, our analysis correlated call recording files with locations data stored on another TheTruthSpy server. We focused our analysis on U.S. states with stricter phone recording laws. These laws require that at least one person on the line consents to the recording or they will be subject to state wiretapping laws. The majority of U.S. states require that at least one person consents for the recording to be made. However, stalkerware is designed to operate without the victim’s knowledge.
We found evidence that 164 compromised devices in 11 states recorded thousands of calls over the six-week span without the knowledge of device owners. The majority of these devices were found in densely populated areas like California and Illinois.
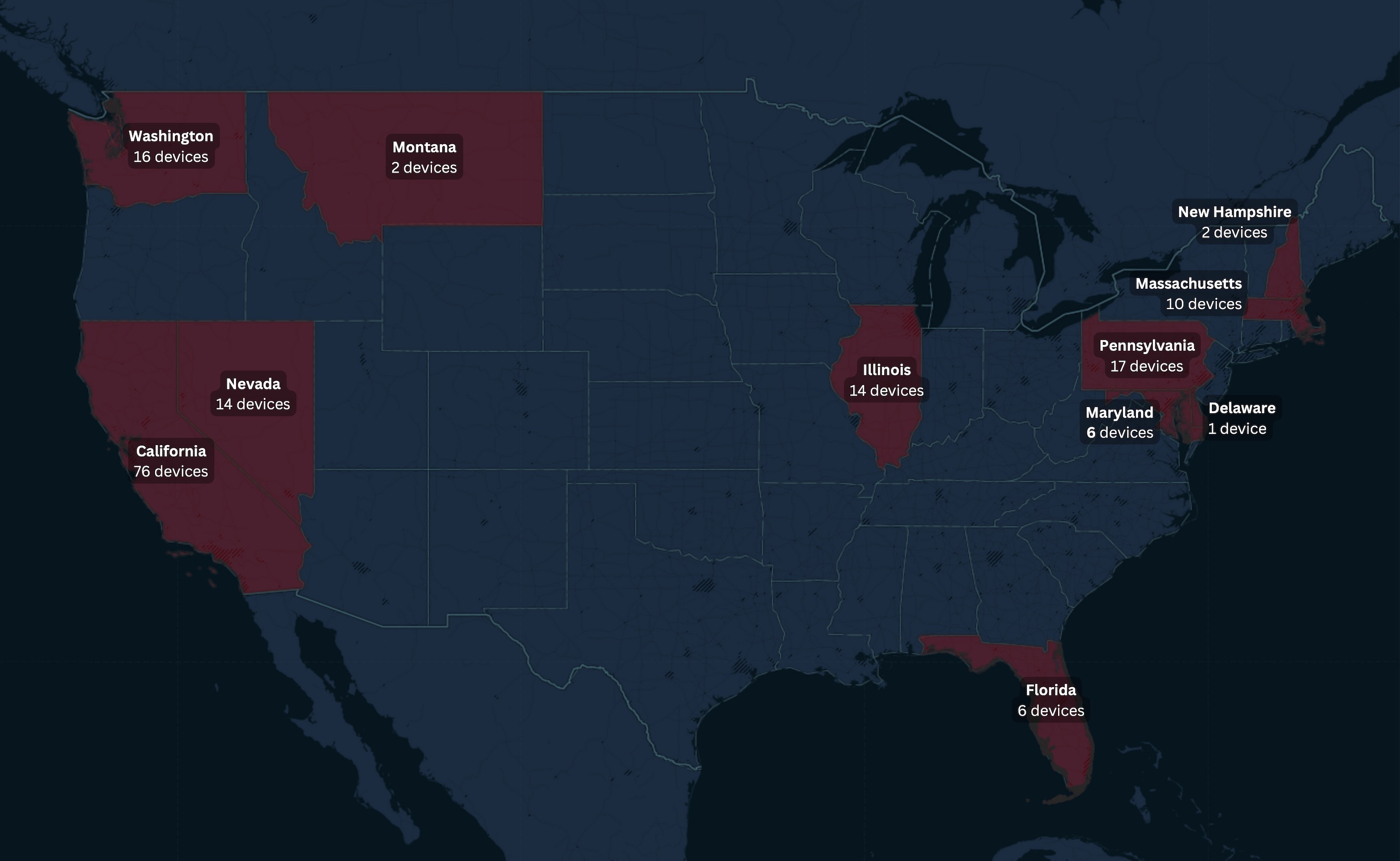
TechCrunch identified 164 unique devices that were recording the victim’s phone calls during the six-week period and were located in states where telephone recording laws are some of the strictest in the United States. California led with 76 devices, followed by Pennsylvania with 17 devices, Washington with 16 devices and Illinois with 14 devices. Image Credits: TechCrunch
The database also contained 473,211 records of photos and videos uploaded from compromised phones during the six weeks, including screenshots, photos received from messaging apps and saved to the camera roll, and filenames, which can reveal information about the file. The database also contained 454,641 records of data siphoned from the user’s keyboard, known as a keylogger, which included sensitive credentials and codes pasted from password managers and other apps. It also includes 231,550 records of networks that each device connected to, such as the Wi-Fi network names of hotels, workplaces, apartments, airports and other guessable locations.
TheTruthSpy is the latest in a long list of stalkerware apps that expose victims’ data due to security flaws which lead to a breach.
While stalkerware apps are not illegal to possess, it is illegal to use them to record private conversations and calls without their consent under federal wiretapping laws as well as many state laws. Although it is not illegal to possess phone monitoring apps solely for recording private messages, stalkerware apps can be abused to spy on phones of spouses or domestic partners.
Much effort is made to eradicate stalkerware by antivirus vendors and cybersecurity companies. The Coalition Against Stalkerware was launched in 2019, and shares resources and samples. This allows information about new and emerging threats to be shared with other cybersecurity firms and automatically blocked at the device level. More information can be found on the coalition’s website about what tech companies can do in order to block stalkerware.
Only a few stalkerware operators like SpyFone and RetinaX have been penalized by federal regulators such as the Federal Trade Commission (FTC). They were charged with enabling large-scale surveillance and using new legal approaches to bring criminal charges.
TechCrunch reached out to the FTC for comment before publication. A spokesperson said that the FTC does not comment on the matter being investigated.
If you or someone you know needs help, the National Domestic Violence Hotline (1-800-799-7233) provides 24/7 free, confidential support to victims of domestic abuse and violence. If you are in an emergency situation, call 911. If you suspect your phone was compromised by spyware, the Coalition Against Stalkerware has resources. You can contact this reporter on Signal and WhatsApp at +1 646-755-8849 or [email protected] by email.